How To Start A Career in Cyber Security

Get to know some of the best ways to enter the cyber security field and how to interact with recruiters. We investigate trends, salaries, and credential ROI
Introduction
I’ve decided to take moment to reflect on who and what were beneficial to me during my journey to become a cyber security professional. In this brief guide, I go over security expertise requirements, best practices, and recommendations for individuals looking to transition into security professionals. This is also a useful pocket guide for recruiters in selecting talented candidates and snuffing out less than credible or incompetent professionals diluting our field. We’re going to cover:
- Briefly comparing backgrounds
- Prerequisite Knowledge
- Understanding just how large the security profession is
- Examine the security foundations, credentials, experience, and trends
- Setting realistic salary expectations
- Spotting good candidates and recruiters for long-term relationships
- Closing and additional resources
My Background
I’m going to provide my background so that you may consider it as you read and compare it with your own as you think about my transition recommendations. My name is Dennis Chow and presently, I’m the CISO of a small consulting group in the Texas region (SCIS Security). I’ve also worked for and with many different employers of varying verticals and sizes. My journey has been moving mostly up from IT general practitioner work and through the the varying stages of security professional titles ultimately winding up in the red team side after many years. In tandem for a time; I was a grunt systems technologist in the Air Force (nothing to do with cyber security).
Note: In our slide you will also see our co-founder and CEO James Davidson of SCIS Security as well. (We work together.)

I’ve always wanted to be some sort of security professional and no one really wanted to take a chance on me despite my interest and projects involving security administration because I was only “IT.” In 2009, I made the public facing transition officially into security as a SOC analyst working rotating graveyard shifts at a company called Alert Logic. Unfortunately, I also had to take a 30K pay-hit to be there.
Luckily, I was still single at the time; but it made it stressful to save, finish school, and pay rent at the same time. The hiring manager threw me a pcap and said “tell me everything you can find about this file.” — it had MS08–67exploitation and man-in-the-middle attacks as I would later investigate and report to even get an in-person interview.
Today, I’m glad to have made the investment during that limited opportunity window and kept hammering away at rounding out my skills as being a holistic and robust security professional. I’ve been lucky to have been part of multiple industry verticals including: healthcare, oil and gas, defense, e-commerce, airlines, and Fortune 100 consulting. And yes, my present salary more than makes up for the first year’s pay cut.
Prerequisite Knowledge Check
This section is going to be brief, but direct. Just like how everyone as a kid wants to become “xyz” such as an Astronaut; many don’t make the cut. It’s not for a lack of effort, or a dream. It’s a combination of opportunity, your existing skill, and aptitude. You need to be ready with self reflected reality check— and if you can even afford to transition right now.
Some hard questions others and you need to ask yourself involve having enough background skill, experience, and aptitude in the following (that you can self-study and achieve business class results without having to be hand held):
- Can you plan and build your own computer from scratch (without using a wizard or cheat guide)?
- Can you make a system image, deploy, and resize partitions?
- Can you write basic scripts in any programming language?
- Do you know the difference between a policy and a procedure?
- Do you know common core command-line syntax for Windows and Linux for system administration without referencing anything?
- Deployments: Do you know how to subnet and deploy a basic business network: including routers, switches, basic firewall rules, email services, and identity federation?
- Are you able to communicate and present information verbally and over written context without others asking what you meant?
- If you’re a IT professional making six figures: Can you afford to take a pay hit to be an entry level security professional?
- Do you have the time, focus, and self-driven will power to study on your own and perform work during non-work hours to keep your craft up to date?
- If given the funding and proper study material; can you pass certificationexams (written and hands on)?
This is a critical junction point: If you said no to any of the above or would have trouble learning all of the above; the hard truth is you aren’t ready for a role in security at all. Some candidates get lucky and have either friend-referrals or can navigate enough interviews with non-technical hiring teams to “get in.” My recommendations assume you have neither going forward. Don’t fret! There is light for those who want to work hard at getting the above skills whom may have a little trouble along the way.
The above are baseline skills you need to set expectation wise before trying to enter this field. Now if you’re wondering why do you see ‘incompetent’ security professionals in our industry — the short of it is no one ever gave those individuals the proper scrutiny. They’re decreasing the value and brand that true security professionals work hard to maintain and elevate.
Preparing yourself if you did not meet the prerequisites
If you’re good with the above bulleted questions and can perform them; skip this section and move on to the next section examining security specific industry standards and trends.
For those of you who arrived at this section still highly motivated to meet basic system level and scripting requirements; please make your way, study, and genuinely master the skills using the following resources. Please be cognizant of yourself and understand that *memorizing is not learning.*
At the end of each exercise, lab, or lesson: if you can’t look at a different scenario or piece of news and cannot apply the concepts in the form of system deployment, actions, or conceptually in a conversation with a lay person — you did not learn the material.
Here are some FREE resources to help you catch up and get your general IT skills up to snuff before you considering to study security topics. Why is that? It’s because you can’t really secure systems and technologies without knowing how to plan, architect, deploy, use, and tune them yourself. You wouldn’t want a surgeon operating on you without hands-on experience right? Neither do employers or customers for security folk.
- SANS Cyber Aces: Great mini boot camp set of labs, exercises, and video instruction on getting your windows, linux, and networking basics out of the way
- Varonis PowerShell Basics: A mini series set of courses and other webinars that provide scripting with powershell for beginners.
- FedVTE (for veterans or current public sector employees powered by CISA under DHS). These lecture series and courseware are “so/so” but offer free CPE’s and another avenue to learn varying cyber security and IT foundational topics including certification prep for the CISSP, CISM, and other CompTIA certs
- LPI Foundations Training: Great general Linux and technology courseware and tutorials
- Microsoft’s EdX Courseware: You can find Windows, Azure, and other enterprise technology
- Petri IT KB: This is a famous go to source for general system administrators focused on Microsoft solutions
- The Lazy Administrator: A great resource that is similar to Peetri and more of a blog of great tips and tricks
- Intro to Cyber Security from Cisco: Cisco’s Net Academy (NetAcad) has been pushing the security agenda and can have useful insights on the security topic as well as instruction regarding how to do so in the Cisco solution world.
- Cisco Packet Tracer: A misleading title. It’s actually just a Cisco solution network emulator that you can build networks with and interact with the equipment virtually as if you were over the wire or physically at the console.
- Palo Alto Networks ACE Learning (EDU-110): The education course is free and at the time of this writing the Accredited Configuration Engineer was still around to take free. Although this focuses on a vendor product. Lots of good concepts such as NAT, Routing, and rule policies apply.
- LinuxCommand Org: This is a step by step interactive shell and guide on using Linux CLI
- PFsense: This is a great community project which allows you to build your own NGFW and Router setup with great features.
- VetSuccess Academy by SANS: For Veterans that are recently transitioned, in the process of, or have NOT worked in any form of IA/CND/IS. You can apply and potentially get some training and certifications. *I wish they had this when I left!
- OSCP Study Group: For those of you hard heads that will go hardcore there’s a great study group. It does primarily focus on the OSCP and obviously hacking techniques but it can be a complementary resource for defending foundations also.
Of course, there’s also the paid routes and you can help shore up skills by achieving certifications like so:
The Security Industry Landscape
The world as a security professional is just like in IT where it starts off as a general practitioner. There are lots of different wording and distinctions that we’d like to address though. I’ve taken this from a slide deck we created for a recruiting agency to help illustrate further. In short, the current industry is broken up into 3 major areas: Infosec, Cybersec, and AppSec. Read our infographic for further details:
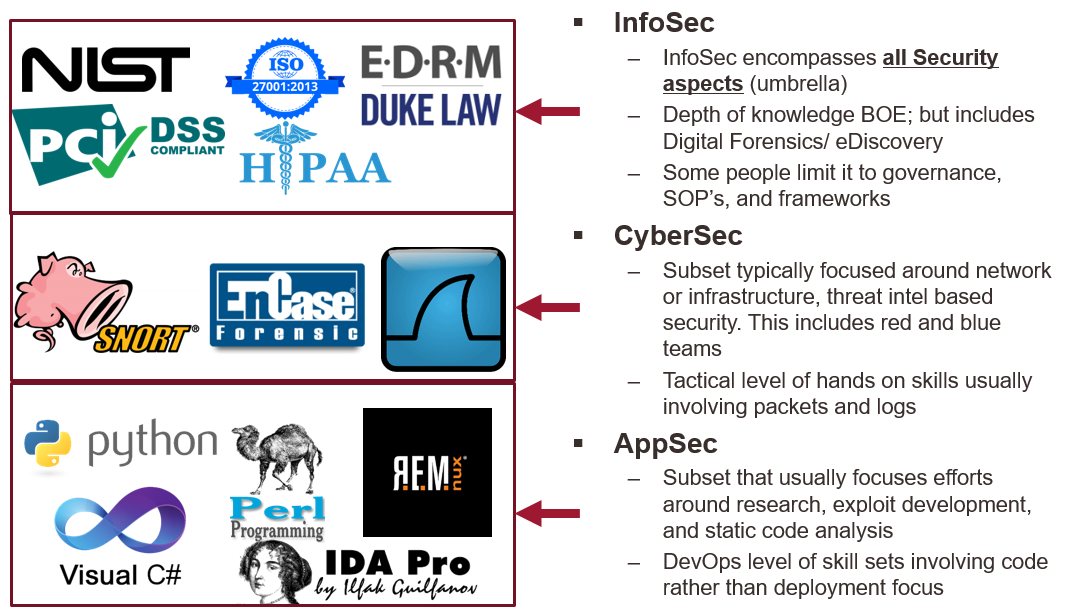
It’s not really a question of getting into “security”and automatically becoming a penetration tester (hacking techniques). Some immediately grab their OSCP and sometimes get a major break. However, it’s more likely you’re going to be starting off in the defender or blue team side of the house. Even though you may want to “hack” things for a living; you’ve got a long way to go.
Penetration testing is actually a specialization within security and one that just like IT foundations; you can’t skip foundational defender skills. Sorry, great red teamers need to know the blue side. How else will you evade security controls as a “hacker” if you’ve never designed and implemented them?
No matter what your end-goal or title desire in security: The well-rounded practitioner will have spent time in all 3 of the above security general areas or have had skills exercised in the above before starting to specialize.
Security Professional Trends and Evolution
So, how do we know trend wise that the above categories and technologies depicted are relevant? Let’s examine what we estimated back in 2018 also taken from our deck:
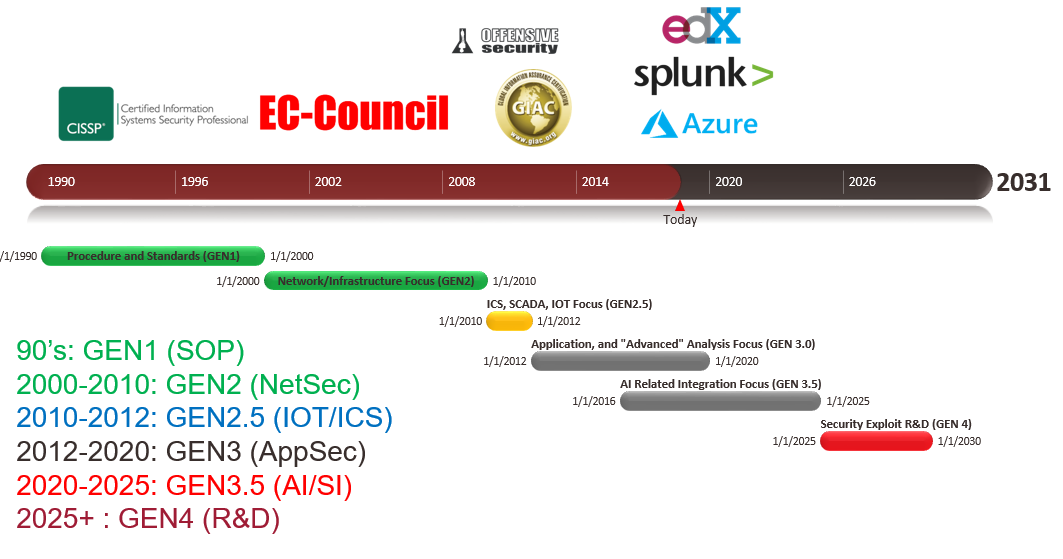
In our brief timeline we depict some popular certification vendors and paths over time starting with the 90’s and the learning topics that featured the most demand and “bang for your buck” from a role to get a high paying salary. As we’ve moved and matured varying technologies and filled roles; the requirement of learning steepened.
In the 90’s the first generation of security professionals paved the way from ground zero. So much of the focus was on documentation, practices, and conceptual procedures that have to be implemented in a program stand point. Today, many of these first gen security professionals that did not transition into other technical skills eventually became architects.The ISC2 CISSP became very popular during this era.
Fast forward into second generation of security; and that’s where I came in on the tail end of it. Network Security was very focused such as firewalls, IPS, and SIEM. In between we also had a sub-movement of trying to learn and extend skills into ICS which was still heavily network security focused but required additional knowledge of industrial professionals to properly monitor and respond on. EC-Council’s CEH is still heavily sought after and the GIAC and Offensive Security certifications such as the OSCP now are starting to take off.
Today, we’re nearing the end of the third generation where the hot commodity skills focused on AppSec roles which include static code analysis, reverse engineering, web apps, API’s, and other heavy automation focused engineering. Between this generation and the next; we estimate that more focus will be on AI and data science driven integration efforts and skills which is a half-step in between. With the focus of data science and AI you see more vendor specific certifications and training which can include Splunk, Azure, and other EdX course ware.
What is beyond security integration and AI efforts in the fourth generation? The highest demand will be us leveraging what we learned from AI and the major skills demand will shift towards security researcher roles where you find vulnerabilities and create exploit proof of concepts.
As you can see; to maintain top pay you’ll continue progressing and be required to learn new and complex skills to stay ahead in our industry. That is the special breed person. A real security professional. Your learning will never stop until you’re ready to start getting paid less over time.
Don’t believe me? Remember in the 90’s and early 2000’s when a mid range desktop support or junior IT system administrator with the A+, Network+ came out making 80K+ a year? For anyone looking now; those roles in many areas are almost paying half! See for yourself: just type in a certification in indeed and examine what the salary ranges are.
Now, compared to our security search results for a ‘CISSP’ in Indeed in 2018 as well as wage employments from O*NET from other DOL data you can see many security roles are on a broad spectrum much higher with many landing 85–130K and if you specialize; this number can easily hit the 200’s. For recruiters, this information was pulled a couple of years ago but isn’t too far off the mark today and will help you determine what are industry general rates for most candidates:

Credentials Matter
One of the key takeaways from this article, if nothing else; is that obtaining and maintaining security certifications matter. Highly recognized education entities include EC-Council, ISC2, SANS (GIAC), and Offensive Security. There’s many others out there include product specific vendor training out there; but you’ll find the above are the ‘big 4’ equivalent for our industry.
It’s not that we’re saying that certifications are your only means of obtaining knowledge. You can do that on your own by joining various study groups, reading tutorials, and practicing with your own lab.
However, just like a degree for many professions — you’re going to need some well known industry standard certifications to attest to your skillsets. And just as important, but rarely discussed — getting specific certifications in a certain order matters as well. I’ll explain more after our next slide below to iterate where most specialization paths lead to in security:
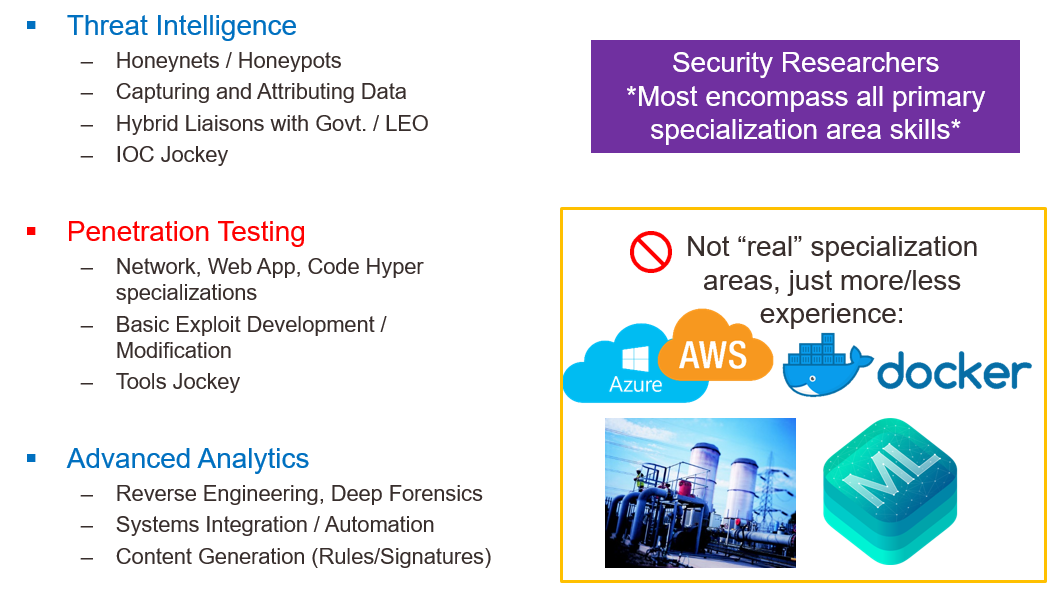
As you can see, the higher the pay you want as a non-managerial specialist; the more skills and spread of knowledge you will have to obtain. But which credentials can help you get noticed if you want to transition in?
My top two recommendations based on recruiter searches and general demand is the CISSP and the GCIH. The CISSP has a wide breadth of learning and is really more of a managerial and architecture position focused certification. Yet, for whatever reason many roles open require or are looking for it. The cost to the exam as I recall was somewhere in the $500 USD range.
The GCIH is for SOC analyst defenders that need to recognize the different type of hacker attacks and be able to properly orchestrate response and handling of the data. That exam depending if you challenge it or take it as part of the official course ware range from $900- $2,000 USD.
Coming in third place is the OSCP and largely because it’s a high value return for the money spent. It does not teach many of the other security foundations and concepts but it’s a great way to get noticed and extend the GCIH knowledge. Keep in mind, the OSCP is not usually for the faint of heart. There are no ‘test questions’; it’s a 24 hour hands on live CTF and another 24 hours of report writing. You could get away with the entire cert for as little as $1,000 USD but that’s all dependent on the individual.
One very important thing to note is that this article is very centered around my experiences in the U.S. market place. As you traverse the globe, the EU and APJ regions seem to recognize CISSP and CEH over GIAC and OSCP. This could be due to a number of geo-political factors including age of the institution operating in the area, cost, and the general presence of the cert. It’s important that you account for your own market’s preference and weigh what you can afford for the cost of course material and examinations in your region.
Does getting the above automatically make you a great candidate? No, not by a long shot. They are just more likely to get you called about your experience and resume. I’ve screen snipped an excerpt from the Training Roadmap from SANS which shows baseline foundations on their own recommended path. I personally recommend the GCIA, GCIH, and GCFA as the trifecta for becoming a solid security analyst before trying to become an engineer in focused roles like pen testing; so you have some minimal hands on expertise.
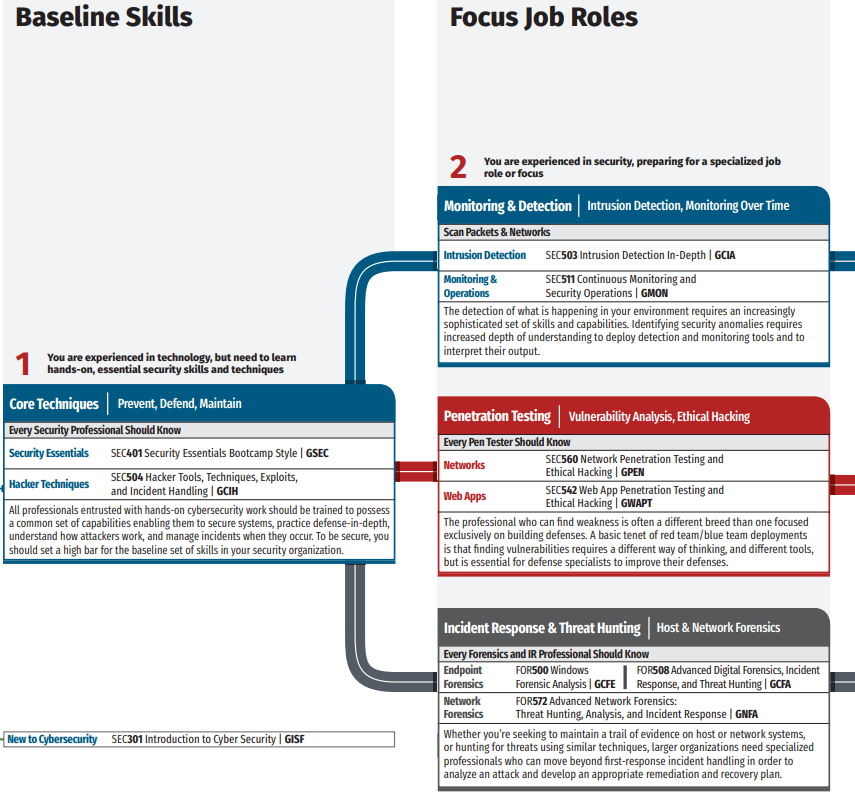
Regardless of what you can afford or which path you want to choose as your own personal preference; certifications make a huge difference in getting your application noticed. Try to get your existing employer to pay for them and point out how the security administration topics align to your day-to-day work and use the big ‘C’ word — compliance. Certifications are one thing, but also, what do you need to do in regards to experience?
Getting your 1–3 years of experience “in” Pre-Game:
Ethically, the only way you can obtain 1–3 years of experience of security related work without being in a paid FTE role is to really be a volunteer first. Sometimes you may get hired, and sometimes you may be retained for project work. But getting a name with a specific “security” specific title such as “security analyst” or “security administrator” even if it is volunteer work can help get you noticed. Here are some great ways to get connected to varying chapters and get some experience in:
- InfraGard Local Chapters: A partnership group at the national and local level between FBI agents and the public to share threat information
- I AM CyberSafe: Volunteer opportunities to teach security to your community
- VolunteerMatch: Find other volunteer opportunities in your area
- Upwork: A market place to bid on varying ‘gig’ opportunities online
There’s plenty of work to be done and as I stated before; without connections and friends to help you with either work or tag you into an interview — this is starting with ground zero and something you can put on your resume.
Working with Recruiters:
Inexperienced candidates don’t realize recruiters are your allies and friends. Not all recruiters are created equal and you’ll want to use your best judgement to work with ones that you both can benefit from growing your professional networks and evolve your career for the long-term. Here are some common complaints that we’ve collected from other security professionals about recruiters they do not wish to be in communication with again:
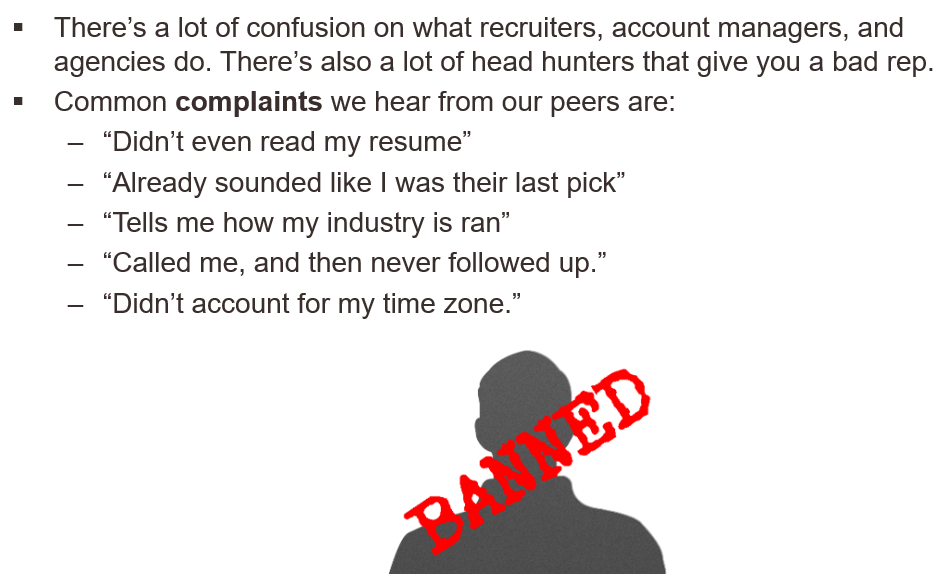
While many recruiting agencies come and go, some of the large ones that can find alot of open requisitions for are from Tek Systems and Robert Half Technology
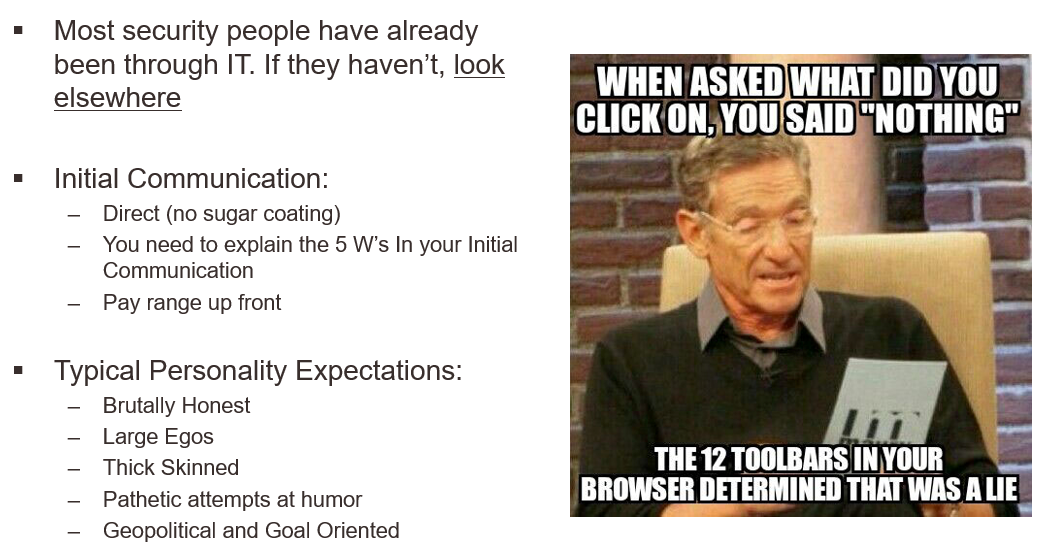
For Recruiters: Personalities to expect from most security candidates
There’s no secret that many security professionals have a smart-mouthed undertone in some of their communications. We suggest to keep in mind the following when you work with some security candidates:
For Recruiters: Who are the good candidates?
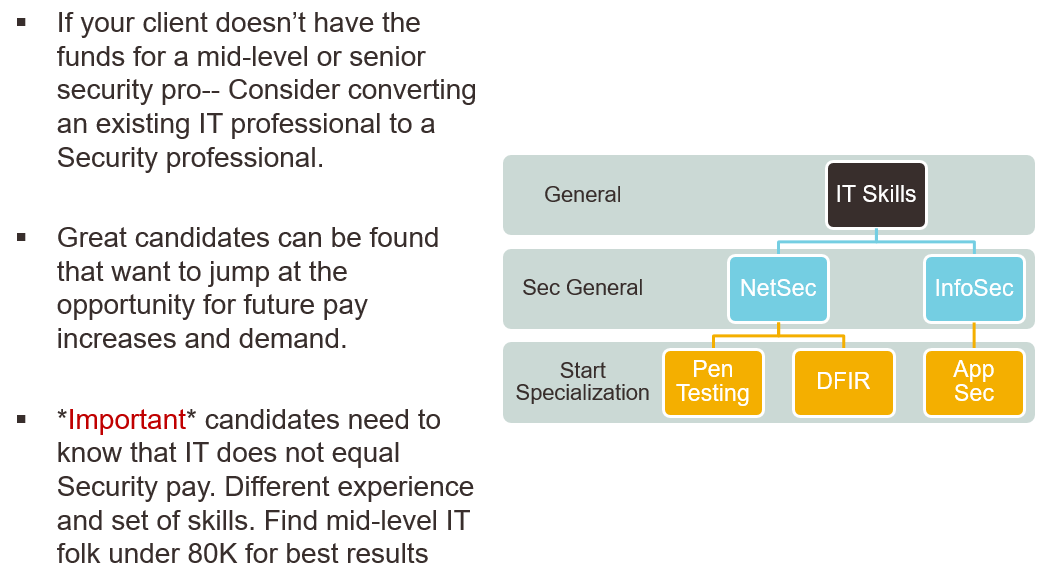
We often work with recruiting agencies to help them better understand where and who to source for talent in security. Based on our experience, we’ve come up with our own thoughts on where you can “phish” for them (pun intended). Sometimes the path of finding a security candidate has to start with a client trusting a potential transitioning IT professional. Here is a general path as we discussed earlier in the article:
Many high demand and frequent roles of talent pools that we noticed in 2018 seem to be around certain areas of the country in the outer rims of the U.S.:
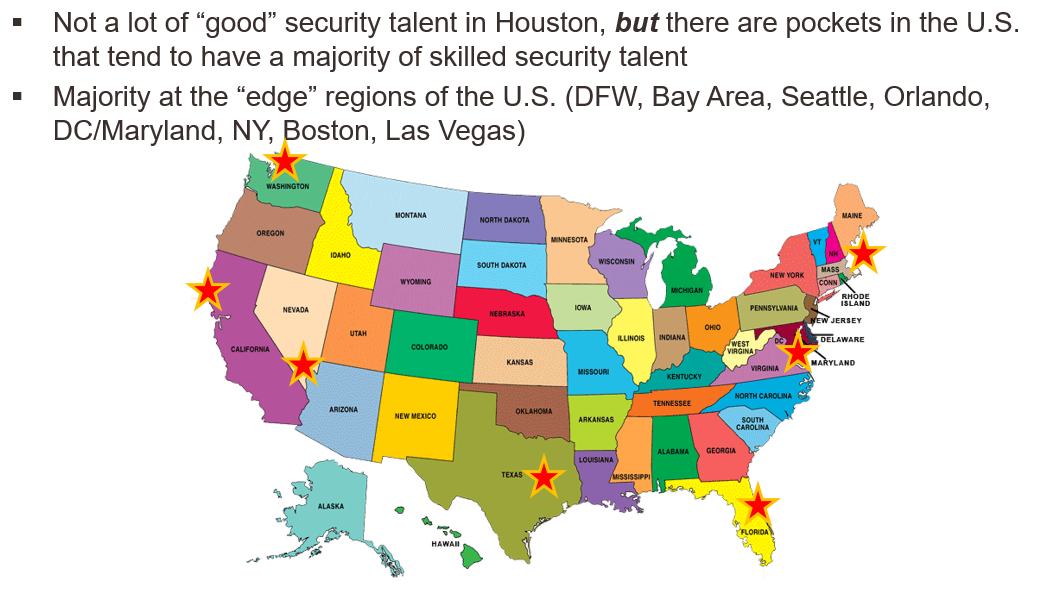
Each star represents a general metro area that we felt had a large amount of demand and well paid roles for security professionals. For ourselves, we were presenting this original deck in Houston and so we had to acknowledge that Houston did not have a great source presence for security talent nor job opportunities compared to the rest of the states. However, it doesn’t mean it won’t change in the future.
Recruiters can also find candidates at varying meetup chapters including Infragard, ISACA, and other local conventions such as B-Sides that bring communities together and lots of entry to mid level talent looking to exchange ideas and prove themselves.
We should also mention that due diligence on all candidates are key. Identifying different levels of embellishment are key to determine if that person will be successful in certain roles or not. We’ve come up with (3) typical types of “fakers” trying to transition to and from security on a regular basis:
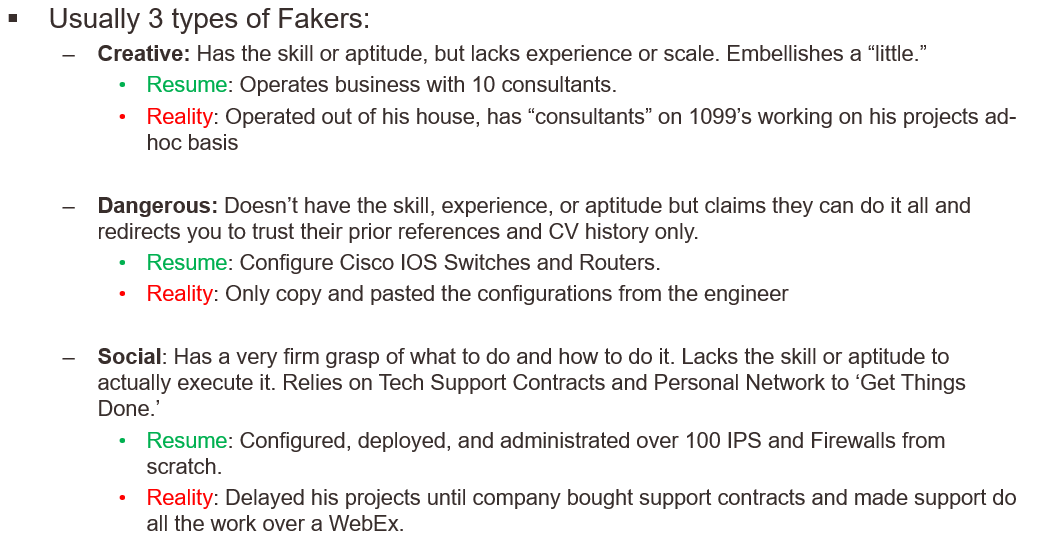
Part of trying to weed out fakers that just don’t know their material happens in the pre-processing stage. Check out their OSINT as it relates to the individual such a screen name or email and just punch into a Google search. You would be amazed at what some candidates come back with. Other checks involve a little more work I highly employ anyone reading this article to always include your certification number when you send in a CV.
Recruiters and employers need to cross validate certifications to ensure you’re 1) Have been certified and 2) Maintain that certification. Here are some links that can help for the any CISSP, GIAC/SANS, and A+, Network+, Linux+, Security+ type certifications:
For Recruiters: So how do we “sell” certain candidates?
Security professionals are among the biggest opportunists one can come across and may come across as job “hoppers.” As I’ve traversed varying agencies, employers, and different roles in the space; I’ve got some ideas on how recruiters can ‘tune’ their communication to help smooth this process over with perspective employers:

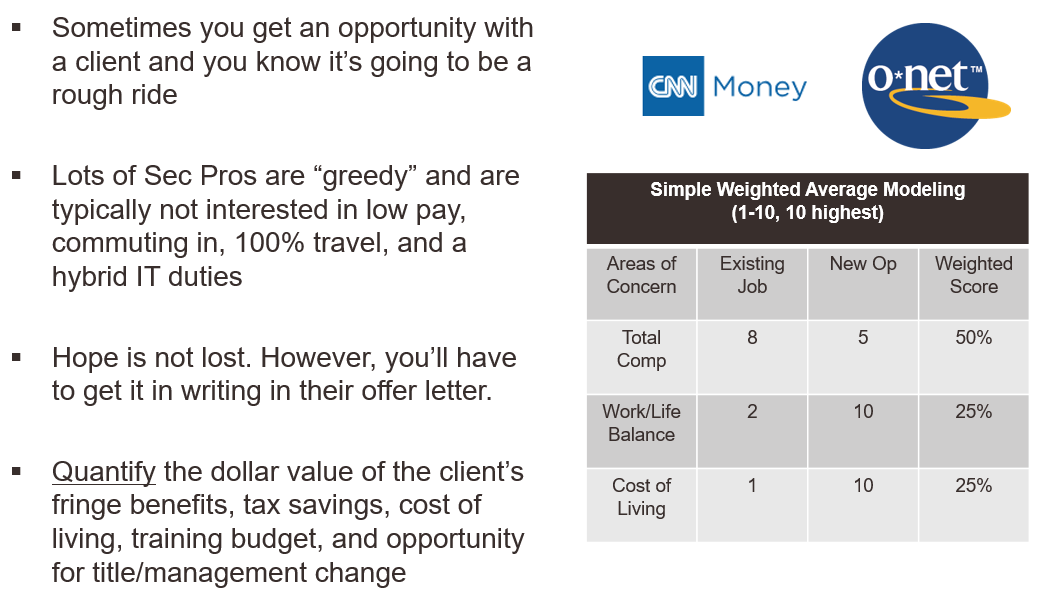
And of course in hard sells; it’s not always the candidate! If you need to help a candidate determine if a role is a good fit or not. Consider providing some other key points for roles that are hard to sell:
For Recruiters and Candidates: Tech Screening
I’m a fan of early screening and transparency so that neither candidate or recruiter wastes time for a requisition. I strongly suggest candidates and recruiters prepare for technical screenings at early stages of their applications prior to submitting to the client (perspective employer). Here are some sample questions from our deck and visual answers to consider when preparing a candidate for submission:
Full animated version at MalwareUnicorn’s RE101 Course
Closing and Additional Resources
I hope you’ve enjoyed some of our perspectives about transitioning into the security industry and how recruiters and candidates can bridge communication differences between themselves. We’re all in it to make our communities safer to operate within cyberspace. As a final resource, I’d like to share a recent series of podcasts from SANS called: “Trust Me, I’m Certified” which airs weekly. It features many well known industry experts and how they entered the field along with some of the struggles they’ve faced, before, during, and sometimes after the security profession.
Please feel free to let me know what you thought of our brief; and as always if you are in need of security expertise consulting or services, please visit us online at: www.scissecurity.com


